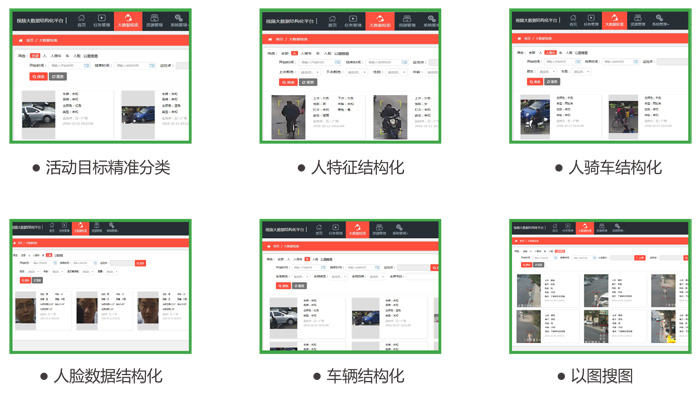
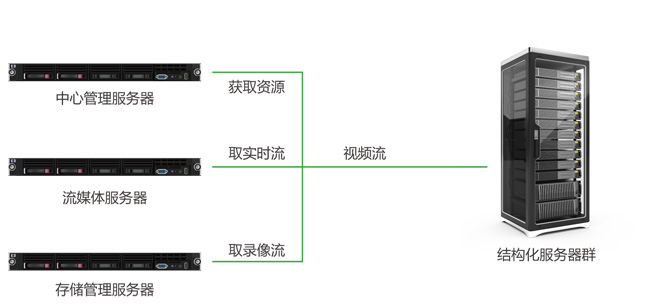
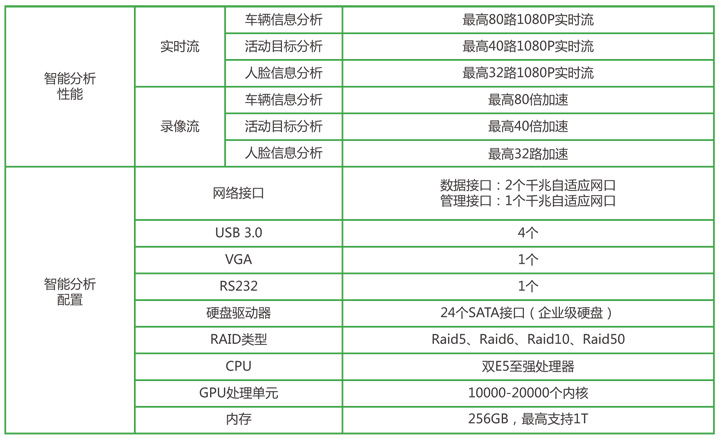
Application of artificial intelligence in security field
Higher quality and Lower Price Carbon Steel/Stainless Steel Pipe Fittings Produced by Jimeng Group.We produce all kinds of Carbon Steel/Stainless Steel Cap,Socket,Cross,and Threaded High Presure Stainless/Carbon Steel Fittings.
Size:DN 10-DN 2000
Standard:ANSI,ASME,JIS,KS,GOST,DIN,UNI,EN,GB
Export Country:US.UK.SERBIA,RUSSIA,ITALY,IRAN,KOREA,JAPAN,SPAIN,CHILE,BRAZIL
SCH NO:5,10,20,30.40,60,80,120,140,160,STD,XS
Welding Method:Seam,Seamless,Half Seamless.
Radius Type:1.5D(Long),1.0D(Short)
Surface Finish:Nature Surface,Sand Blasting,Painting.
Material:SS 304/304L/316/316L/201/430,CS Q235/A234/Q195/A105/20#/16MN
Certificate:ISO-9001,KS,CE



Steel Pipe Fittings
Stainless Steel Cap, Carbon Steel Cap, Carbon Steel Socket, Threaded High Pressure Steel Fittings
Hebei Jimeng Highstrength Flange-tubes Group Co.,Ltd. , https://www.jimengflange.com
